RedMimicry is a semi-automated platform that enables your team to emulate realistic cyberattacks, effectively testing and enhancing your clients’ cyber defenses against the latest threats. By implementing advanced techniques, tactics, and procedures (TTPs), RedMimicry ensures that your security assessments are comprehensive, relevant, and effective.
RedMimicry complements your specialized post-exploitation tools by offering a versatile repository of initial access scenarios modeled after real-world threat actors.
Integrating RedMimicry into your Red Team operations enhances service delivery, reduces tooling and infrastructure overhead, and maximizes team productivity.
Benefits
Benefits of RedMimicry for Red Teams
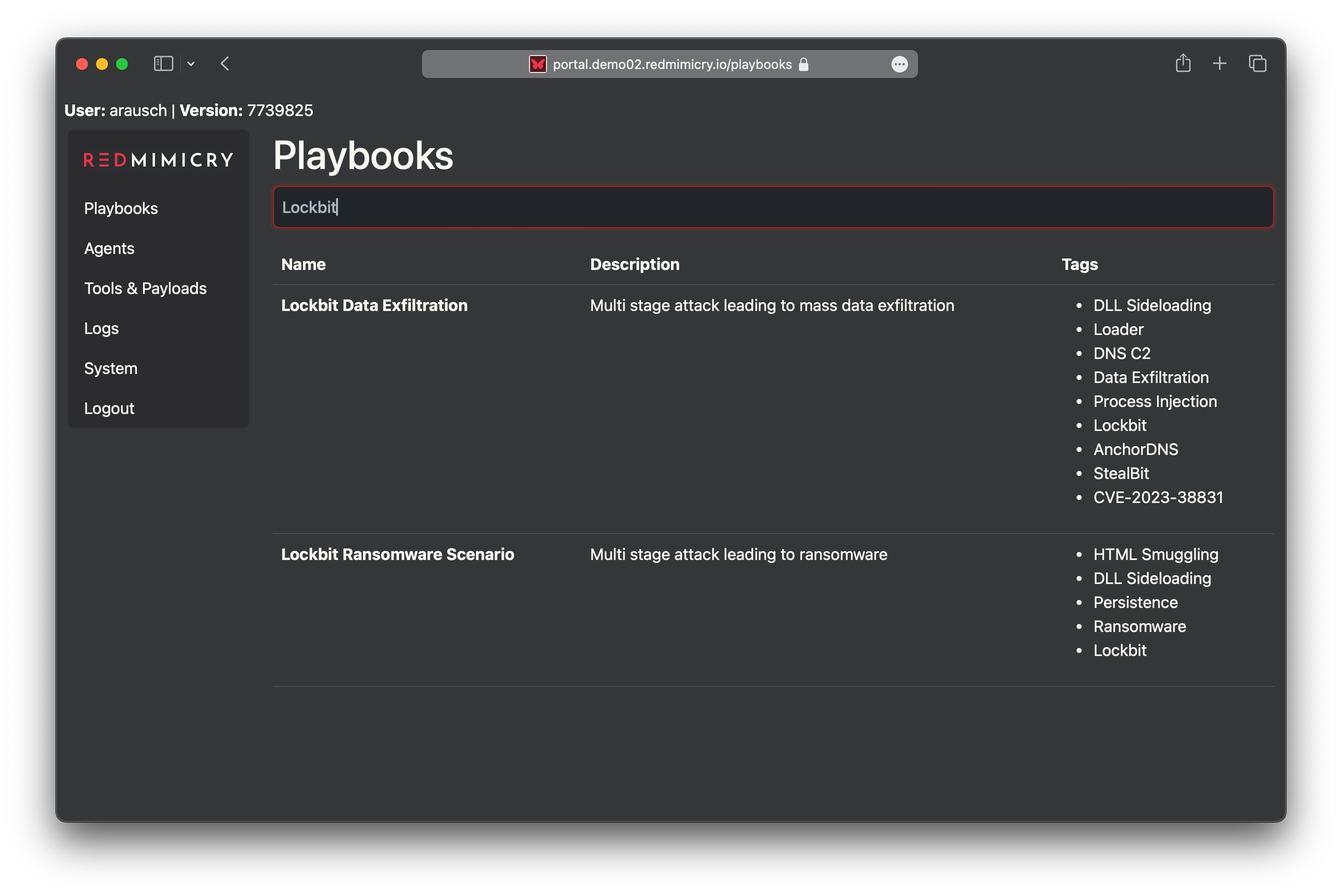
Initial Access Playbooks
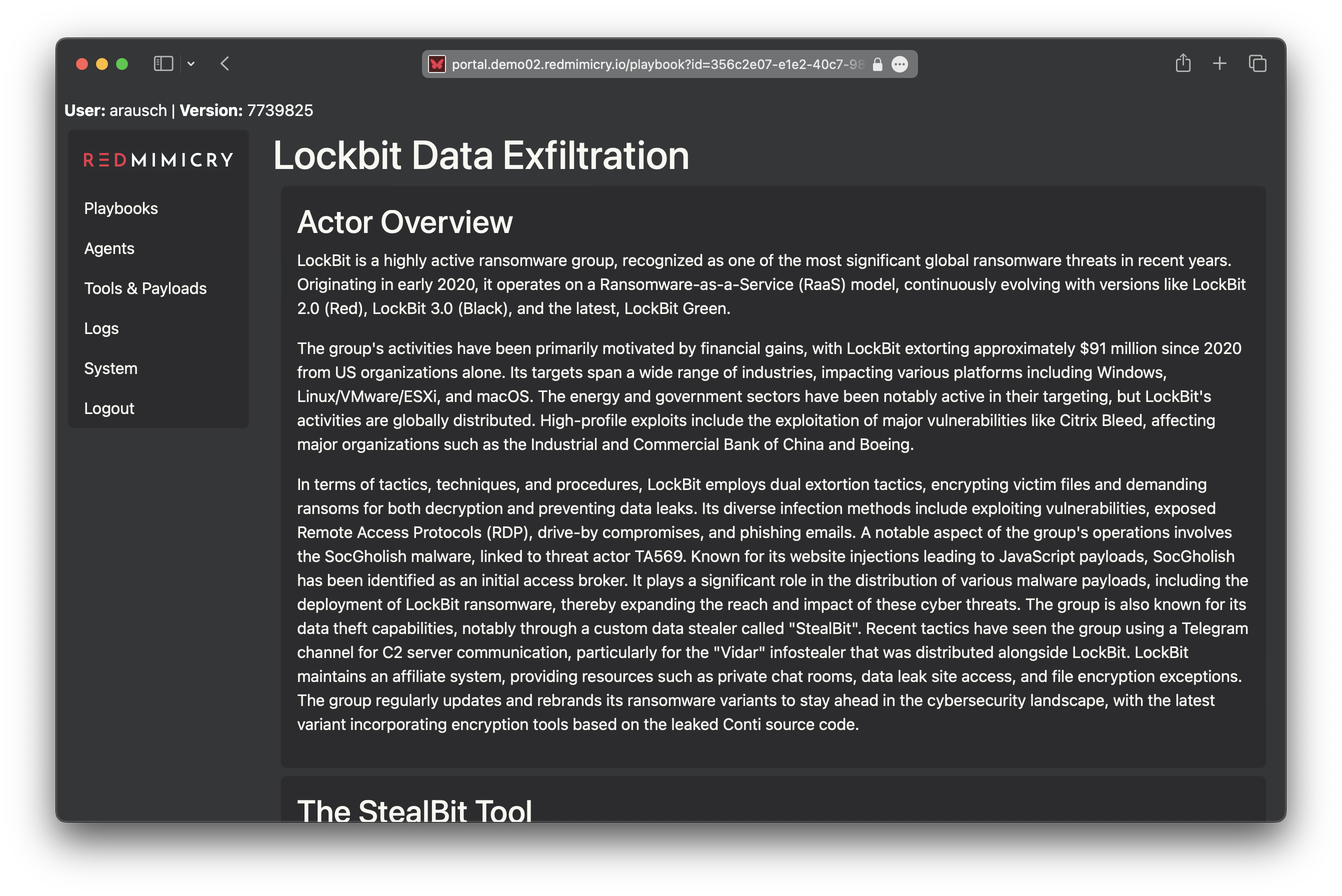
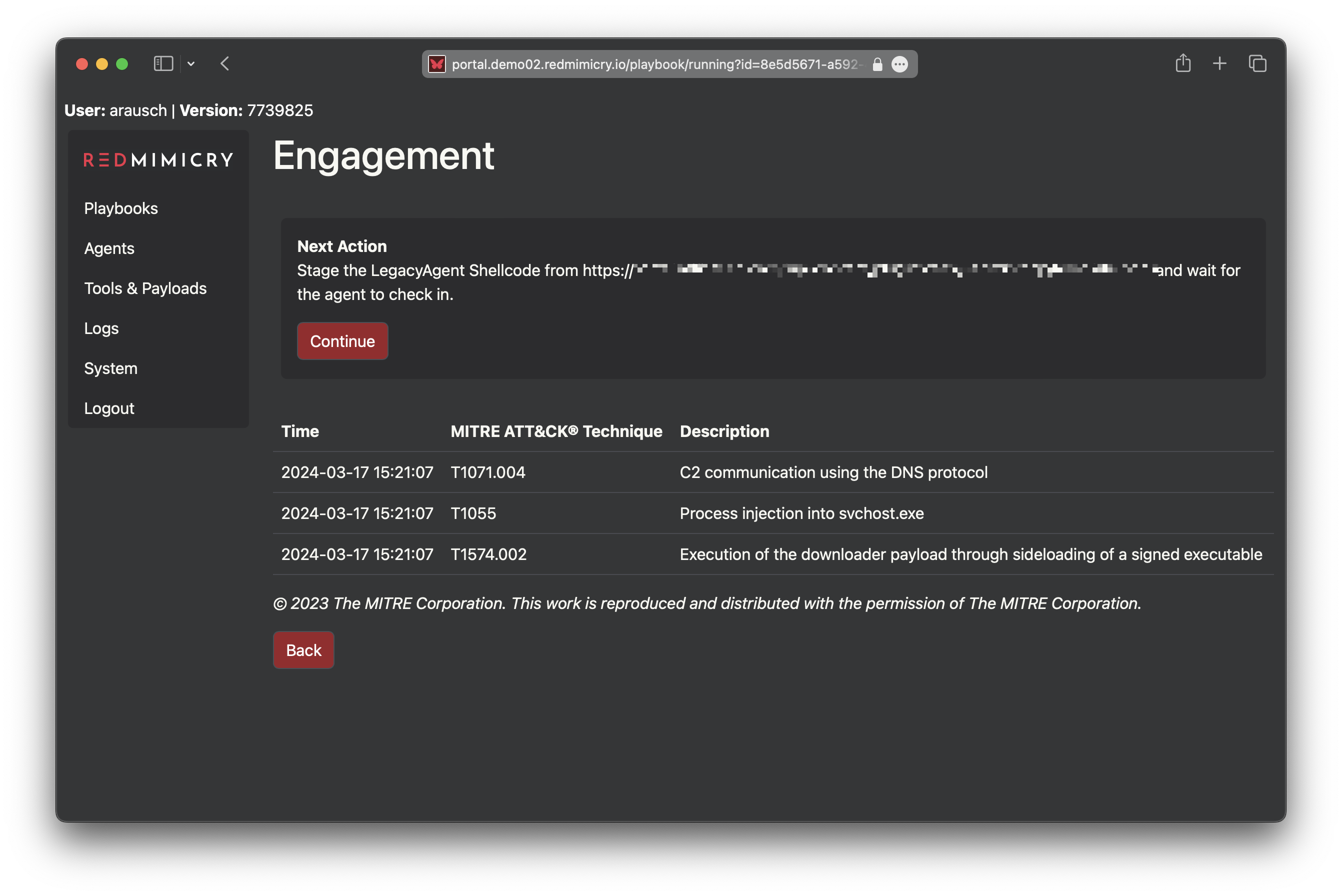
RedMimicry provides playbooks that emulate realistic initial access scenarios and post-exploitation activities on compromised systems. Active agents deployed throughout the playbook can be controlled through an interactive shell, allowing real-time engagement. Additionally, many agents support in-memory staging of user-provided payloads, enabling operators to continue engagements with their own tools.
Maximize Your Team’s Productivity
Your team’s time is best spent on developing highly specialized post-exploitation tools rather than on the development and maintenance of initial access scenarios. RedMimicry allows this focus while keeping you updated on the latest initial access TTPs from relevant threat actors.
No Infrastructure Hassle
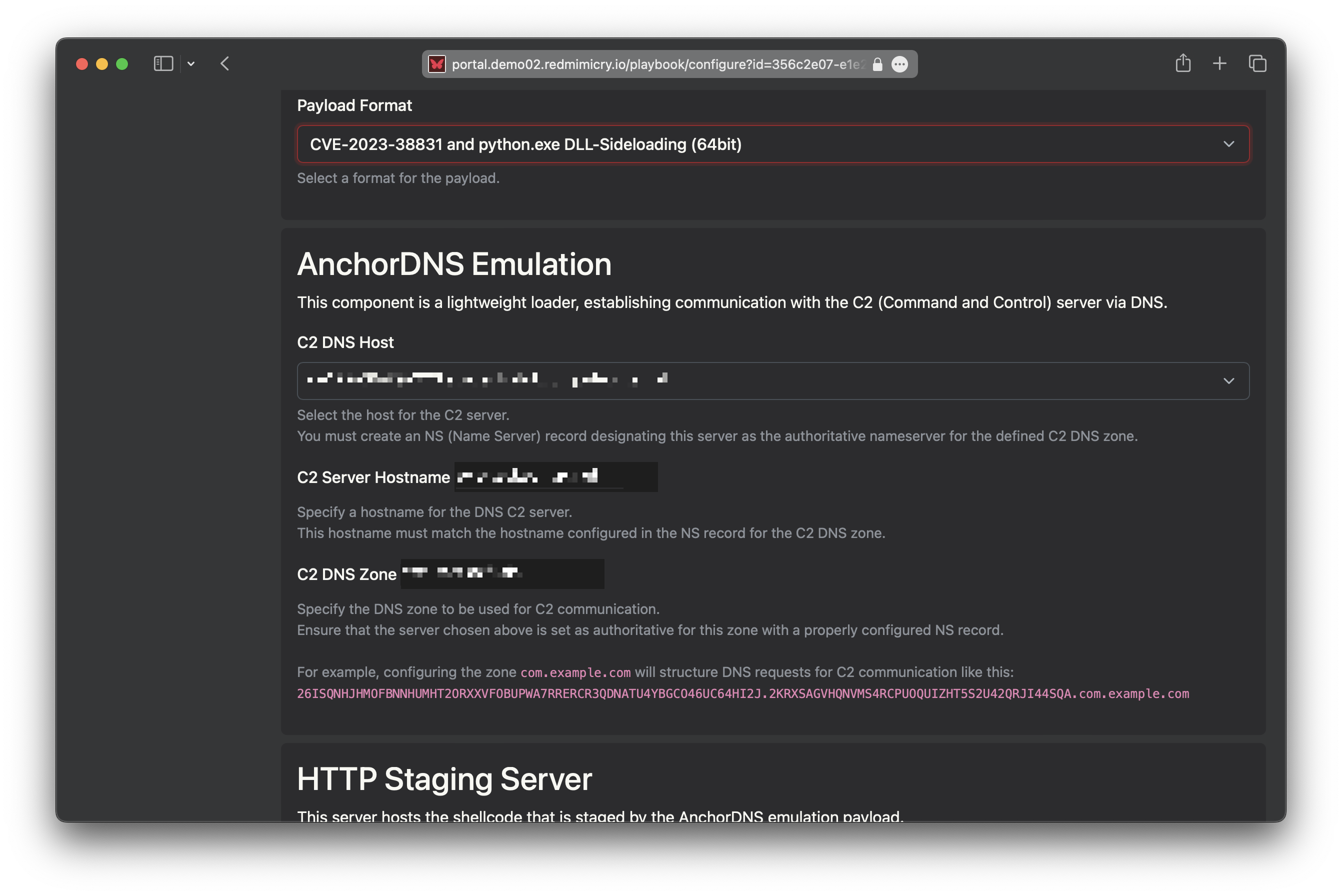
RedMimicry automatically deploys C2 endpoints, staging services, and other infrastructure required to run the playbooks. This significantly reduces your team’s pre-engagement setup time.
Continuous Updates
Stay ahead of emerging threats with RedMimicry’s regular content updates. We frequently add new scenarios and update existing ones to reflect the latest TTPs used by real-world threat actors, ensuring your red teaming activities remain current and effective.
Comprehensive Testing with Minimal Effort
RedMimicry simplifies the process of conducting comprehensive tests on your clients’ cyber defenses. Our platform supports a wide range of endpoints, including Windows, macOS, and Linux, enabling thorough coverage. This allows you to efficiently challenge and validate your clients’ defenses.
On-Premises Deployment
RedMimicry can be deployed on-premises, ensuring that you have full control over the platform and its data.
Next Steps
Next Steps
To request a demo of RedMimicry’s capabilities, request a demo or contact Stefan Steinberg .
