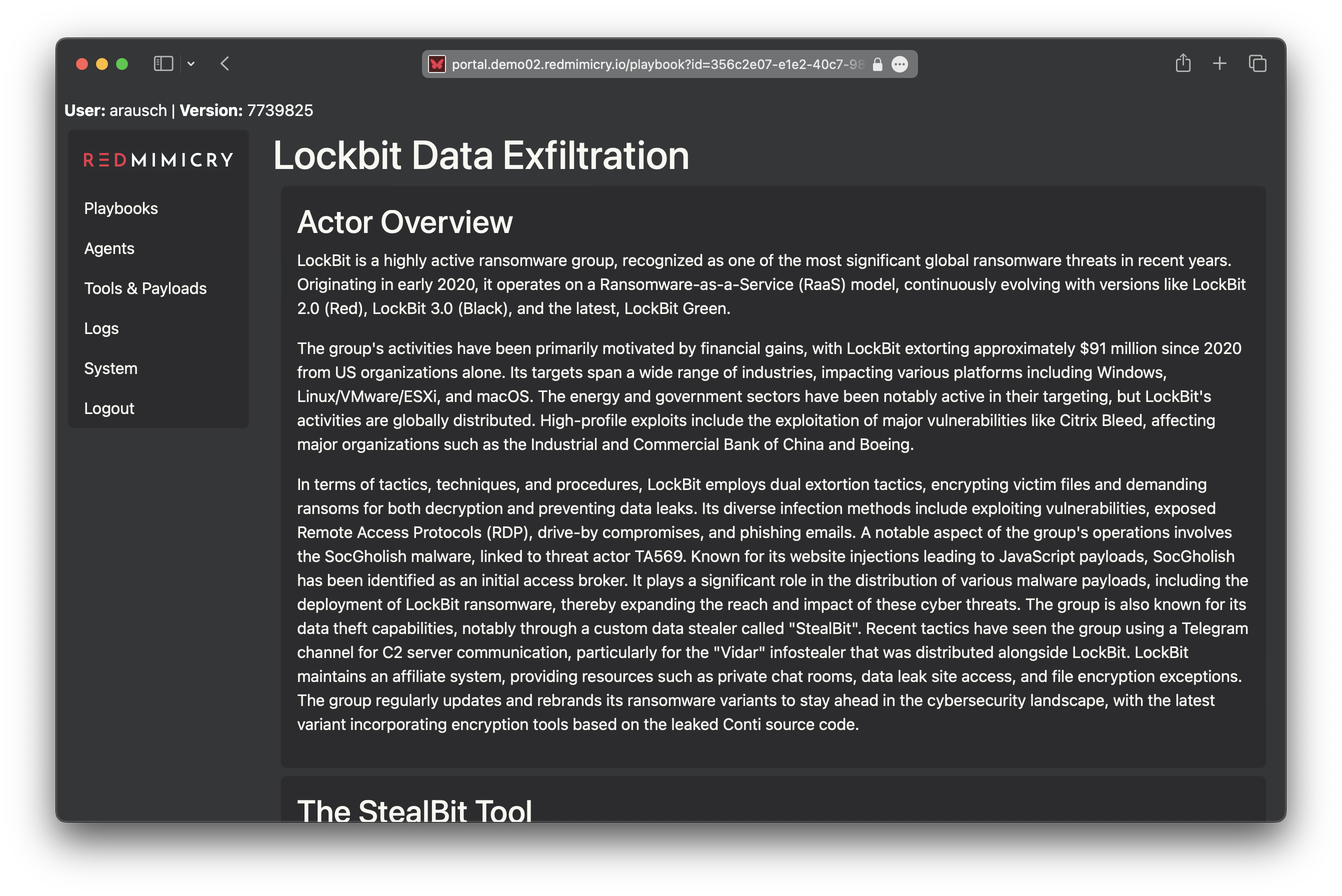
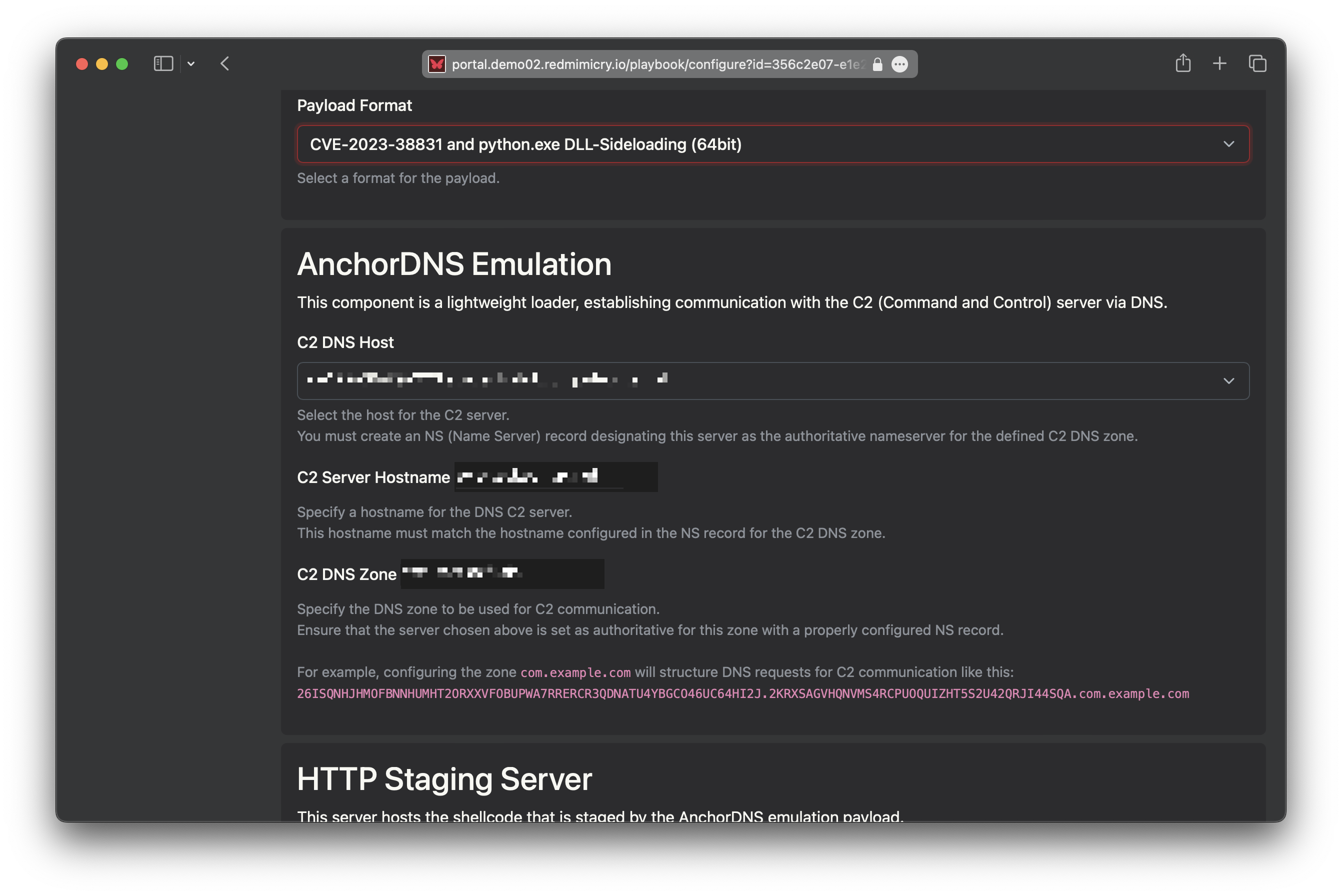
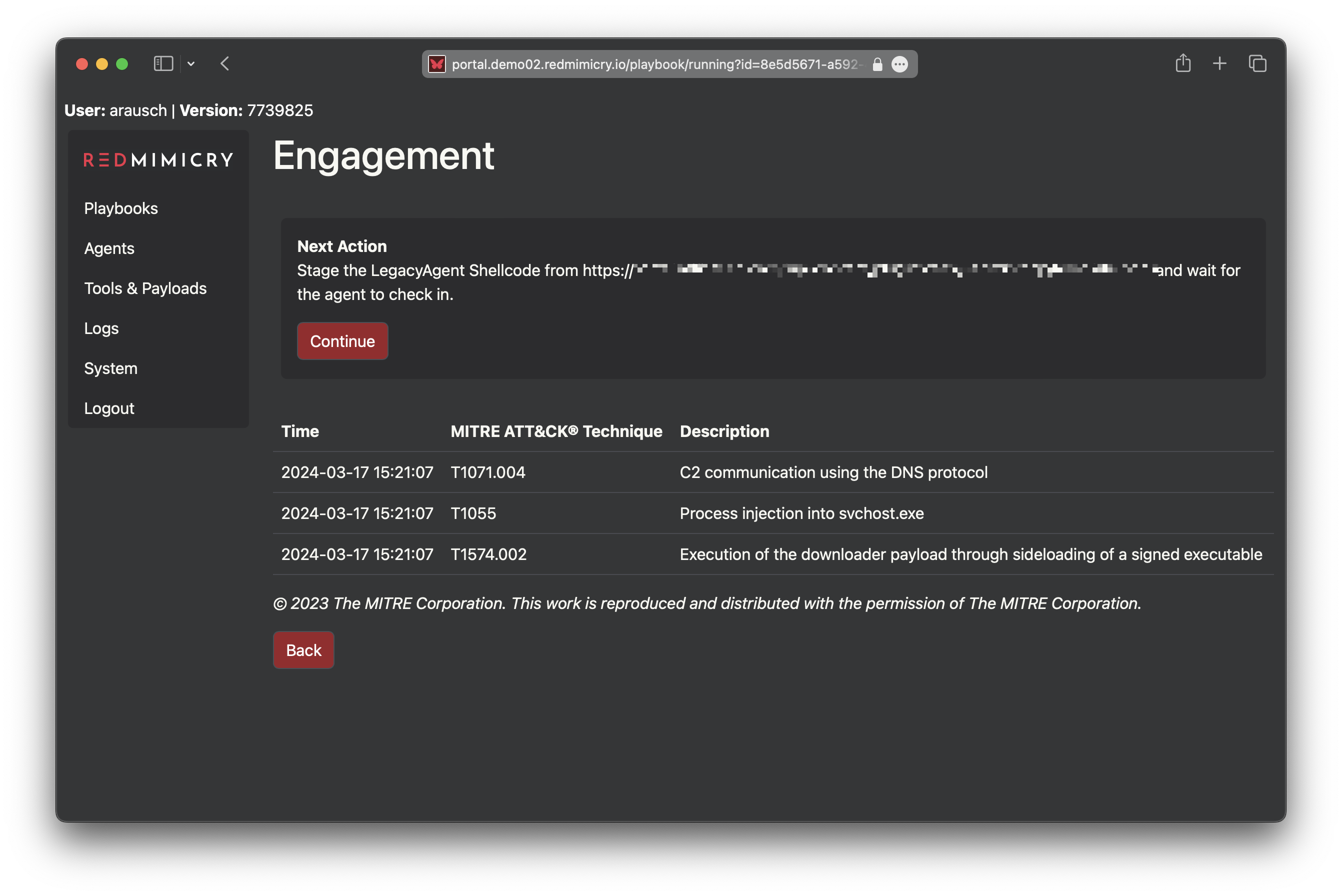
RedMimicry is a breach and attack emulation software that includes scenarios emulating realistic threats such as ransomware and supply chain attacks. Through RedMimicry’s web interface, you can execute these scenarios on endpoints within your network.
Assess the detection and blocking capabilities of your security toolchain and evaluate the effectiveness of your response processes.
RedMimicry emulates realistic attack chains, including C2 communication, allowing you to test endpoint security components like antivirus (AV), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR), as well as Network Detection and Response (NDR) systems.

Use Cases
RedMimicry supports various use cases, including cybersecurity solution testing, process validation, and analyst training.
Analyst Training
Training and Internal Exercises
Realistic threat emulation maximizes training results for your SOC and CERT.
By emulating realistic cyberattack scenarios, RedMimicry enables teams to practice and refine their response strategies against the latest threats. The platform’s regularly updated scenario library ensures comprehensive and current training. Additionally, the user-friendly interface allows staff to configure and control complex attack simulations.
Tool Strategy Validation
Tool Strategy Validation
Ensure your security investments are effective.
Organizations invest heavily in security tools, and it is crucial to validate these investments before a real attack occurs. RedMimicry allows businesses to simulate multi-stage, complex threats that mimic real-world cyber actors, assessing the effectiveness of their Endpoint Detection and Response (EDR), Security Information and Event Management (SIEM), and other monitoring systems. This validation helps identify potential capability gaps and enhances the organization’s overall security posture.
Process Validation
Process Validation
Strengthen and validate your security processes effectively.
RedMimicry excels in validating security processes, ensuring every step of your incident response plan is robust and effective. The platform allows for step-by-step execution of attack scenarios, providing visibility into each phase and enabling the monitoring of response measures.
Usage
Library
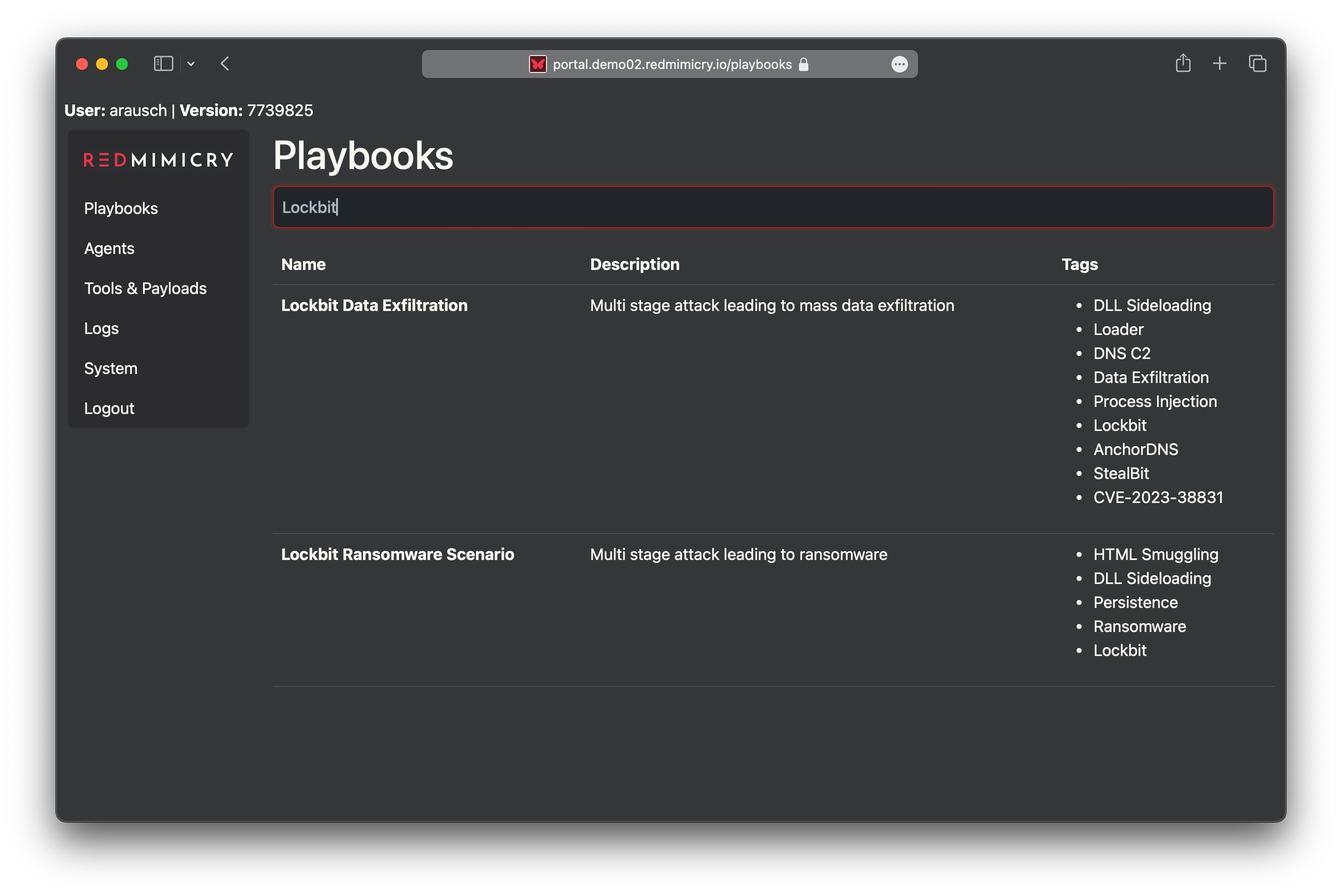
Playbooks
Select a playbook from the library to run. All playbooks are tagged with the techniques used.
Benefits of RedMimicry
RedMimicry vs. Cobalt Strike
RedMimicry vs. Cobalt Strike
RedMimicry offers a comprehensive, user-friendly, and continuously updated solution that eliminates the complexities and resource demands of custom setups required with Cobalt Strike.
Unlike Cobalt Strike, which is only a building block of a realistic attack chain, RedMimicry provides a wide range of realistic, ready-to-use attack scenarios through an intuitive interface, accessible even to less experienced users. This approach saves time, reduces operational overhead, and ensures consistent, high-quality emulations of current threats, allowing organizations to focus on improving their defenses rather than on building and maintaining attack tools.
RedMimicry vs. Penetration Tests
RedMimicry vs. Penetration Tests
RedMimicry allows for continuous testing rather than the periodic, one-time evaluations typically provided by external penetration tests or red teaming.
While external tests offer valuable insights, they represent only a snapshot in time. RedMimicry enables organizations to perform ongoing assessments on their own terms and schedule, ensuring that defenses are consistently evaluated and improved against evolving threats. This continuous approach maintains a high security posture between external tests, enabling quicker identification and mitigation of vulnerabilities. By integrating RedMimicry, organizations can achieve a proactive security strategy, complementing external testing with robust, regular internal validation.
RedMimicry vs. Breach and Attack Simulation
RedMimicry vs. Breach and Attack Simulation
RedMimicry operates differently from Breach and Attack Simulation (BAS) software such as XM Cyber. It is a semi-automated solution that focuses on emulating cyberattacks through realistic scenarios reflecting current threats. In contrast, BAS software is typically fully automated, continuously simulating the tactics, techniques, and procedures (TTPs) of cyber attackers to identify vulnerabilities and security gaps across an organization’s network.
RedMimicry is particularly valuable for purple-teaming and training exercises, as it allows for step-by-step execution of an entire attack flow, closely mimicking a real cyber attack. While BAS tools cover individual TTPs, they do not provide a fully realistic picture of a complex, multi-stage cyber attack. BAS tools are excellent for hardening systems and networks by identifying and mitigating vulnerabilities. RedMimicry complements these tools well, as it tests the effectiveness of the hardening process in a realistic, practical manner.
Next Steps
Next Steps
To request a demo of RedMimicry’s capabilities, request a demo or contact Stefan Steinberg .