RedMimicry is your go-to solution for consulting companies specializing in purple teaming services. Our semi-automated platform enables you to test and strengthen your clients’ cyber defenses against the latest threats. With RedMimicry, you can conduct thorough, frequent security assessments, ensuring your clients are always ready for real-world attacks.
In today’s fast-changing threat landscape, relying solely on infrequent security checks isn’t enough. Regular and thorough testing with realistic cyberattack emulations is essential to uncover vulnerabilities, enhance response tactics, and maintain robust defenses.
Key Features
Key Features
RedMimicry is a powerful tool for security professionals specializing in purple teaming. It offers a semi-automated platform that enables realistic emulation of attack chains, allowing you to thoroughly test and enhance your clients’ cyber defenses against evolving threats.
Core Features
No Internal Tool Development
RedMimicry reduces the need for specialized offensive security engineering, allowing you to focus on delivering top-tier security services without the burden of tool development.
Comprehensive Multi-Platform Coverage
Assess your clients’ defenses across Windows, macOS, and Linux with diverse testing scenarios, ensuring that their Security Operations Centers are well-prepared for real-world threats.
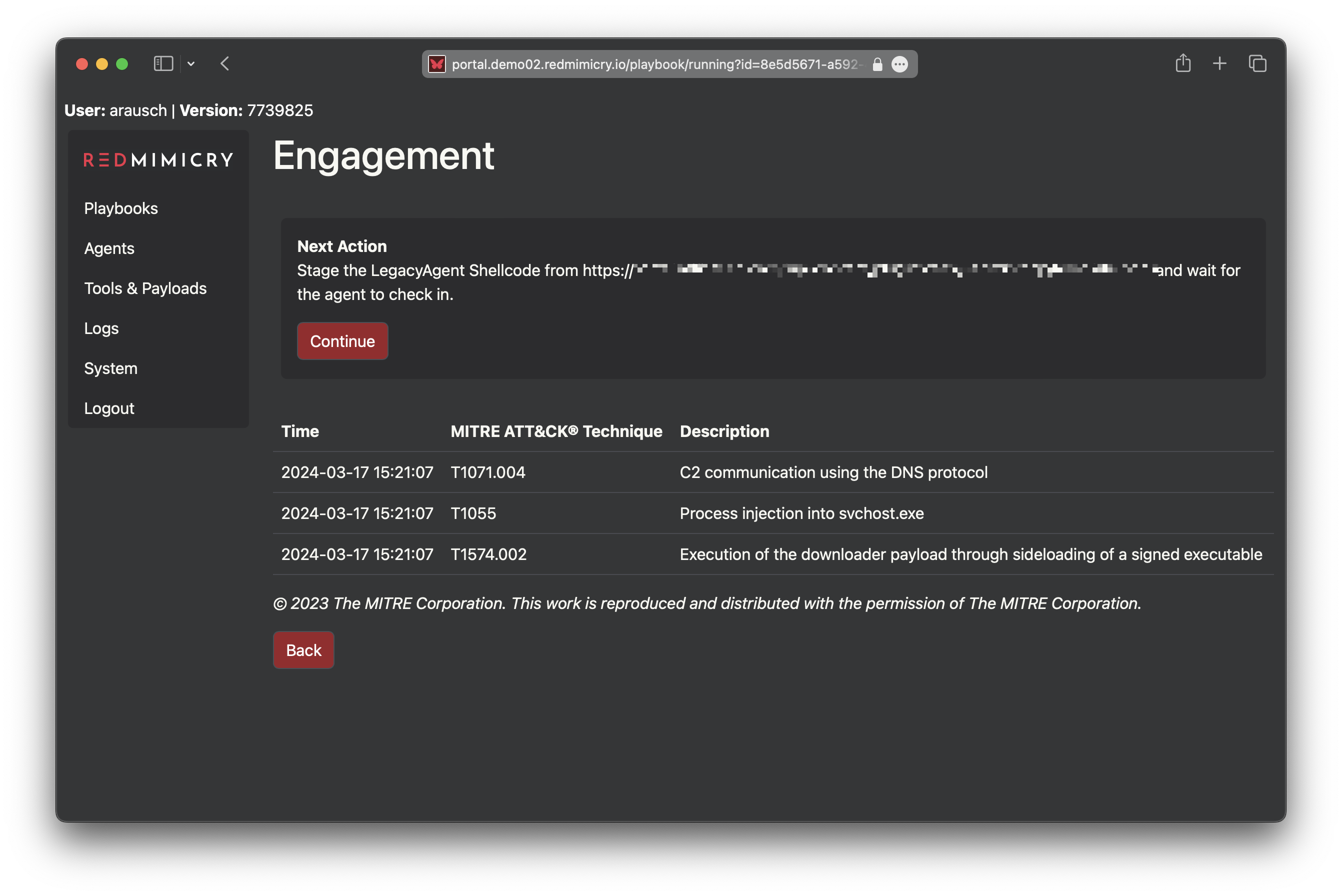
Realistic Threat Emulation
Simulate real-world Tactics, Techniques, and Procedures used by threat groups like LockBit. RedMimicry allows you to escalate from basic to advanced attack scenarios, rigorously testing your clients’ defenses.
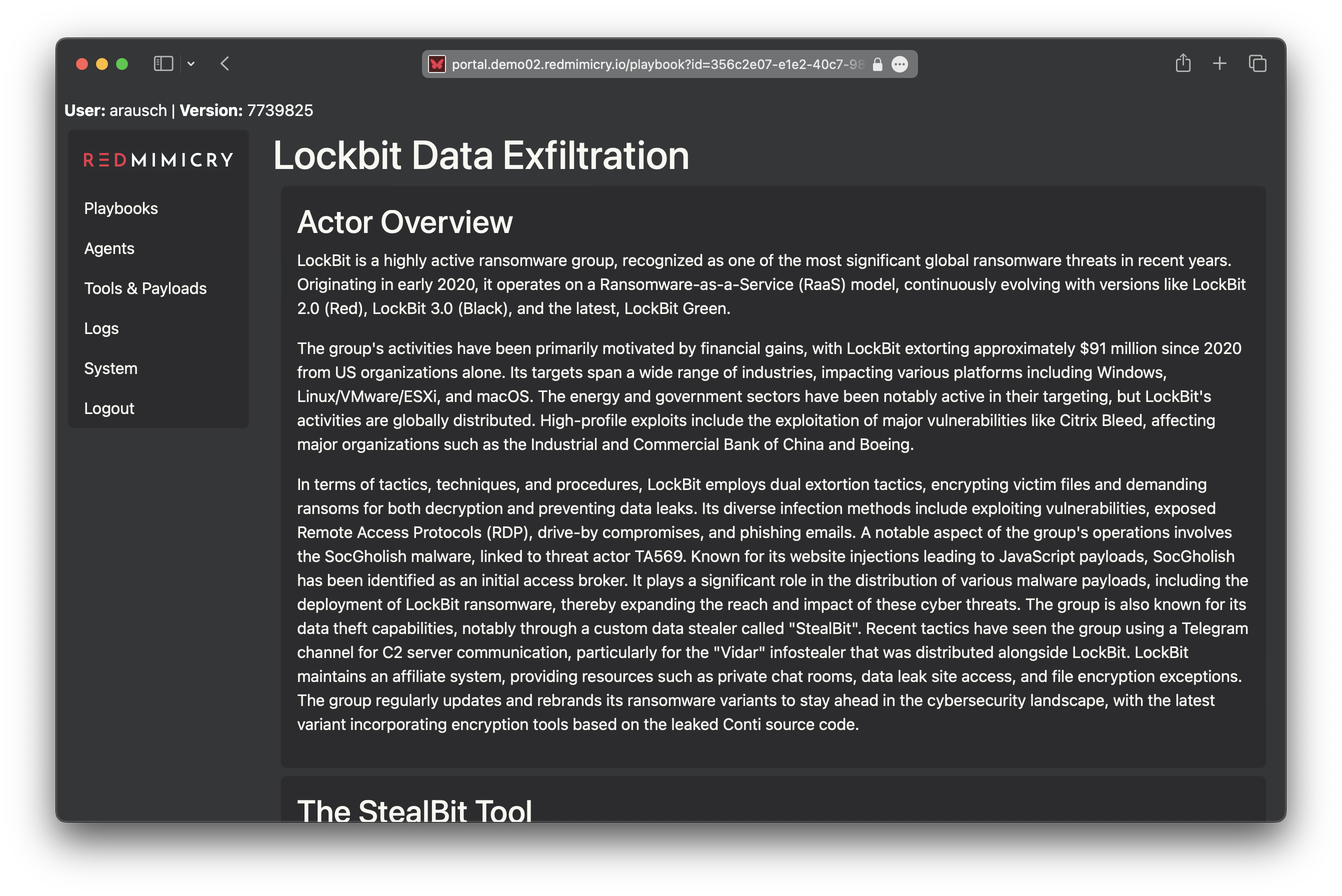
Intuitive User Interface
Easily navigate and control emulations through an intuitive web interface. The interactive agent console offers flexibility for manual intervention, enabling tailored testing scenarios.
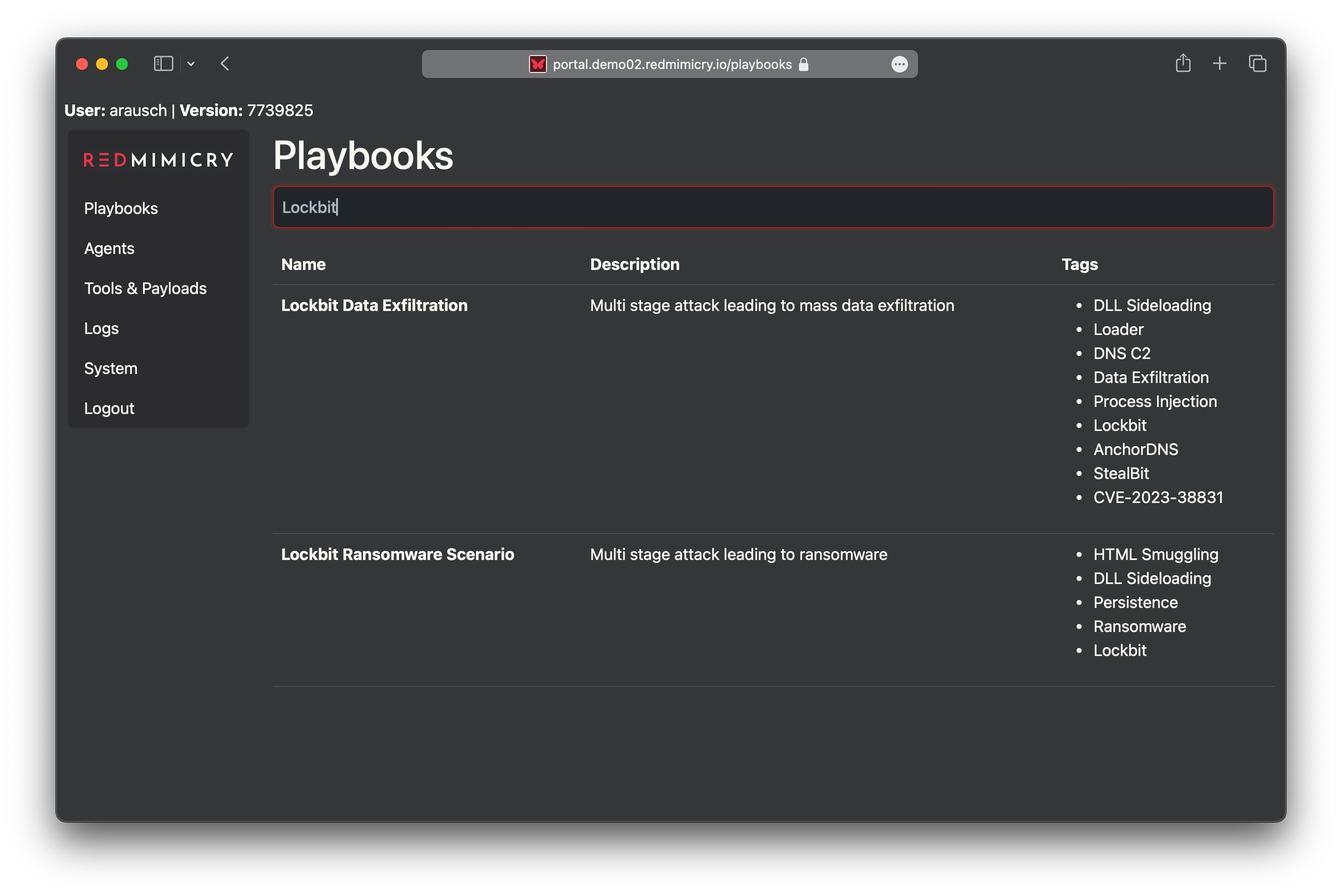
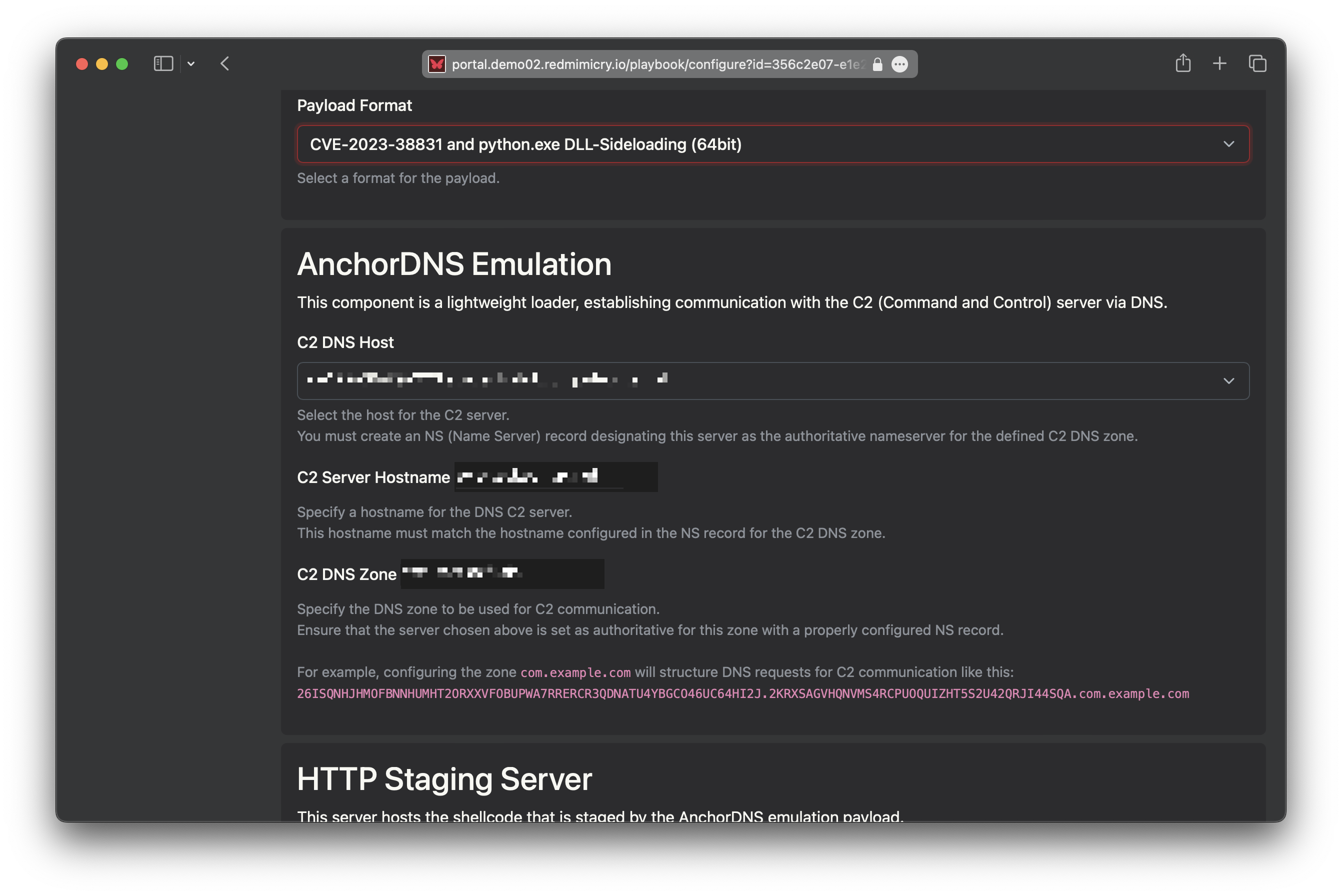
No Infrastructure Pain
Test multiple playbooks with minimal effort thanks to RedMimicry’s versatile edge nodes, which can serve as both Command and Control (C2) and staging infrastructure, depending on the scenario.
Continuous Content Updates
Stay ahead of emerging threats with frequent updates to RedMimicry’s existing scenarios, along with the addition of new ones, ensuring your testing capabilities remain effective and up-to-date.
Flexible Deployment Options
RedMimicry offers both on-premises and SaaS deployment, allowing you to choose the solution that best fits your security consulting environment.
Why RedMimicry?
Simplify Your Operations
Eliminate the complexity and expense of developing your own tools. RedMimicry’s ready-to-use platform reduces operational costs and simplifies service delivery.
Focus on What Matters
Concentrate on consulting and improving your clients’ security postures, rather than on tool maintenance. RedMimicry handles the development and upkeep, allowing your team to focus on delivering results.
Adaptable Infrastructure
RedMimicry’s scalable infrastructure supports a wide range of scenarios, enabling consistent, high-quality assessments without needing to reinvent the wheel for each engagement.
Continuous Improvement
Benefit from ongoing updates that keep RedMimicry at the cutting edge of breach and attack emulation, ensuring you have the most effective tools available.
By choosing RedMimicry, you streamline operations, maximize productivity, and deliver superior value to your clients, all while avoiding the complexities and costs associated with developing your own tools.
Next Steps
Next Steps
To request a demo of RedMimicry’s capabilities, request a demo or contact Stefan Steinberg .
